We analyzed data from the national vulnerability database to assess the applicability of on-device security features
Whether they are discovered by independent researchers, manufacturers, or cyber attackers, device vulnerabilities traditionally have been remedied via patching. Although reactive, patching’s effectiveness is easy enough to quantify: It is effective if the vulnerability no longer exists after the patch is applied.
A host-based defense is another matter. It comprises technology that monitors a device’s function and issues alerts or remediations whenever malicious activity is detected. It does not remediate vulnerabilities: Rather, it defends against exploitation of an undiscovered or unremediated vulnerability.
As such, the host-based security apparatus’s effectiveness can be harder to evaluate than patching. There are several methods, including listing the controls enforced, mapping to a threat model, red teaming, or measuring the effectiveness of host-based defenses against current or likely, in the field, near-term attacks (“proven in use”).
And while “proven in use” evidence has obvious value, it is difficult to gather on host-based defenses (such as RBS’s Symbiote technology). The publicly available data on actual attacks is small, and there is good reason to believe it is often obscured or not released publicly.
Vulnerability disclosures provide some insights, as we can at least determine what types of attacks might be mounted against each vulnerability class. But no matter how severe it is, a device vulnerability only indicates a plausible means for a cyber attacker to gain a foothold on a device. Furthermore, the ongoing reality of zero-day vulnerabilities, which are not detected until a cyber incident is underway, requires a different way of thinking about, and defending against, attacks.
One way is to extrapolate from vulnerability data. This approach depends on several assumptions:
Host-based security is predicated on the need to move beyond a continuous cycle of patching. Vulnerabilities will always exist, and while the reactive patching process will continue to play a role in device security, it simply is not capable of deflecting a subset of threats that are not discovered or can’t be patched.
To evaluate host-based defense, we’ve used raw data published by the U.S. Cybersecurity & Infrastructure Security Agency-CISA on its ICS-Cert Advisories page. The entries include a rating based on the Common Vulnerability Scoring System (CVSS); risk evaluation; affected products, a Common Weakness Enumeration (CWE); and a vulnerability overview/analysis. The analysis is the key component that allows us to determine whether or not an attack launched against this vulnerability would be detected if a host-based defense technology was in place on the device.
Host-based security can benefit end users and original equipment manufacturers in terms of total cost of ownership and reputation:
Assessments of a host-based defense’s ability to detect and/or prevent attacks exploiting any particular vulnerability rely on the ICS Advisory’s risk evaluation, which highlights the class of weakness (CWE) to which the vulnerability belongs, and the consequences of the vulnerability’s exploit (e.g., remote code execution, buffer overflow, denial of service).
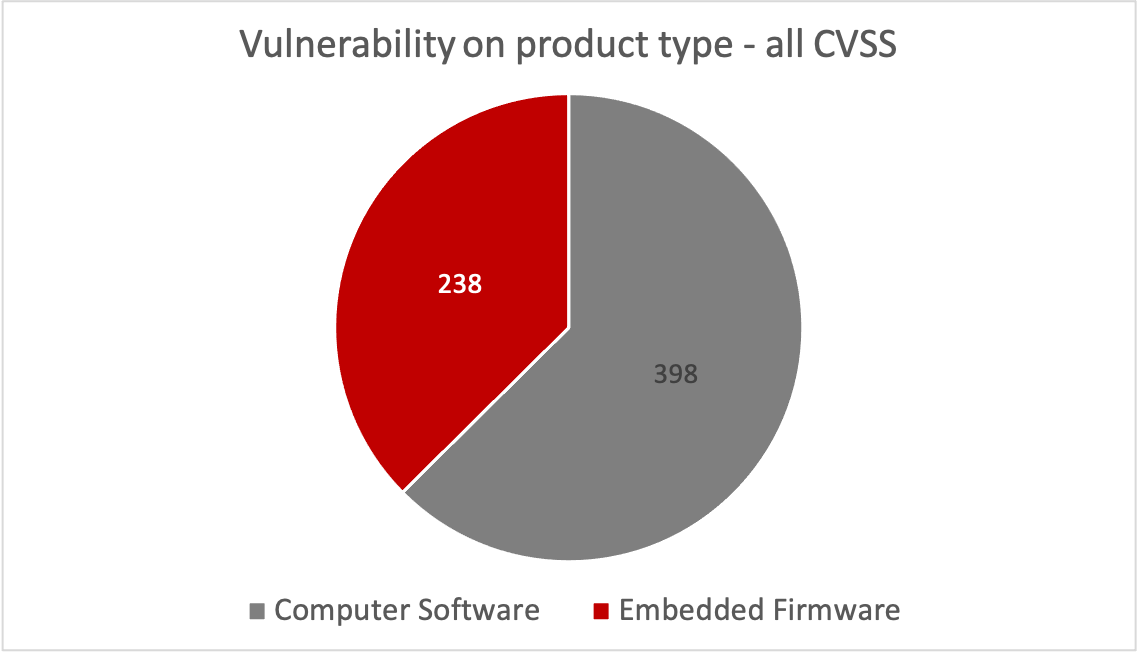
We reviewed approximately six months of ICS-Cert vulnerability disclosures. Of these, 37% were found in firmware.
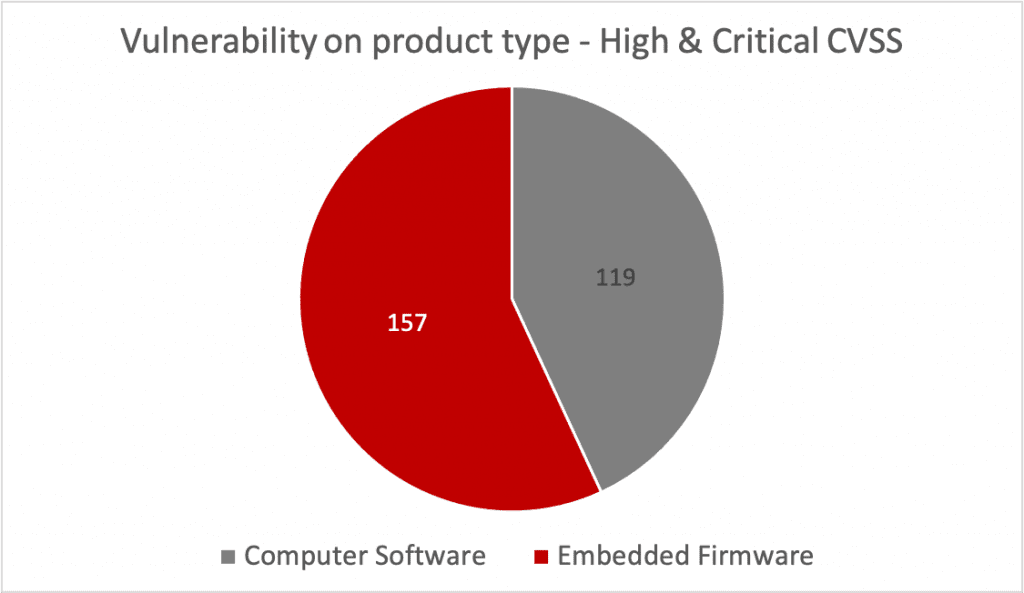
Of the vulnerabilities with CVSS categorizations of “high” or “critical,” almost 57% (157 of 276) are firmware-based:[1]
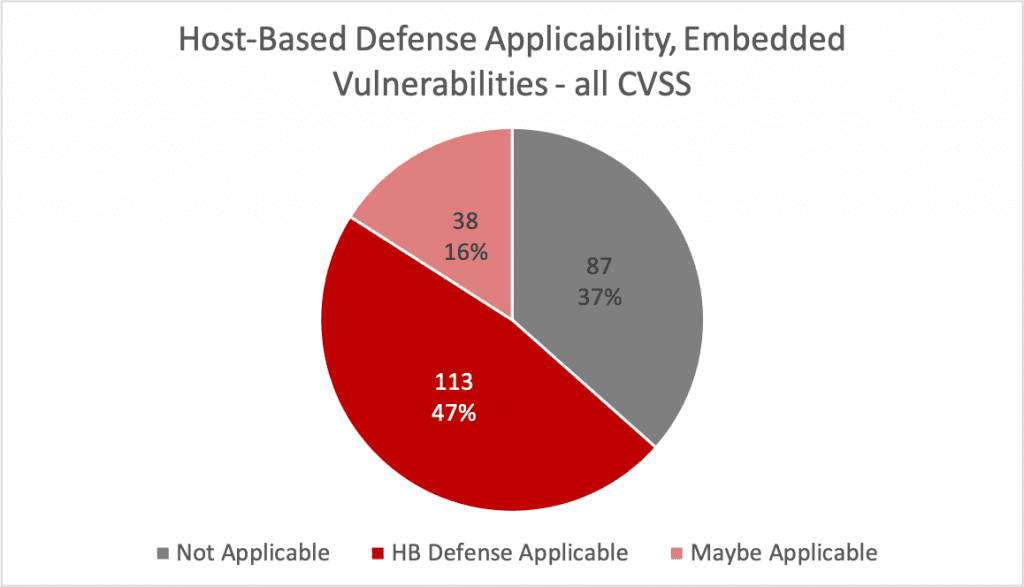
In our analysis, a host-based defense would be effective protection against 63% of these vulnerabilities, including all CVSS severity levels:
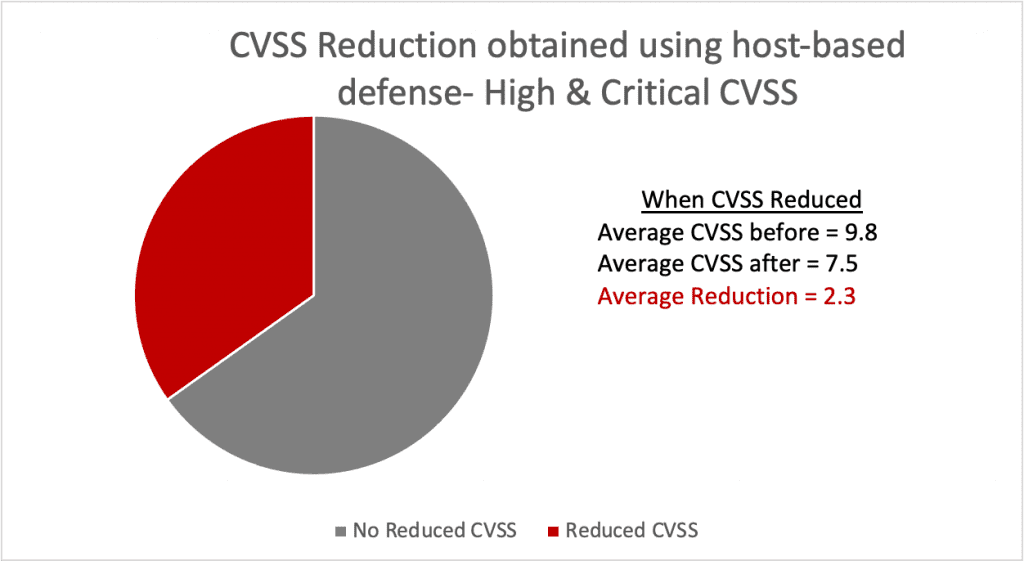
However, of the “high” or “critical” CVSS firmware vulnerabilities, a host-based defense could remove an attacker’s opportunity to reliably execute code or modify memory as part of an attack. It would be applicable or likely applicable on 26% of these vulnerabilities, and would reduce the CVSS rating for roughly one out of three, with an average decrease of 2.3 points on the CVSS scale.
More importantly, applying a host-based defense can reduce the severity of compromises to device integrity, confidentiality and availability. With CVSS vectors, a successful exploit would give an attacker the ability to gain full visibility into the devices’ functionality, and the ability to manipulate files and to deny access by legitimate users.
Our analysis found strong or universal host-based defense applicability with improper input validation, improper command injection, and classic buffer overflow:
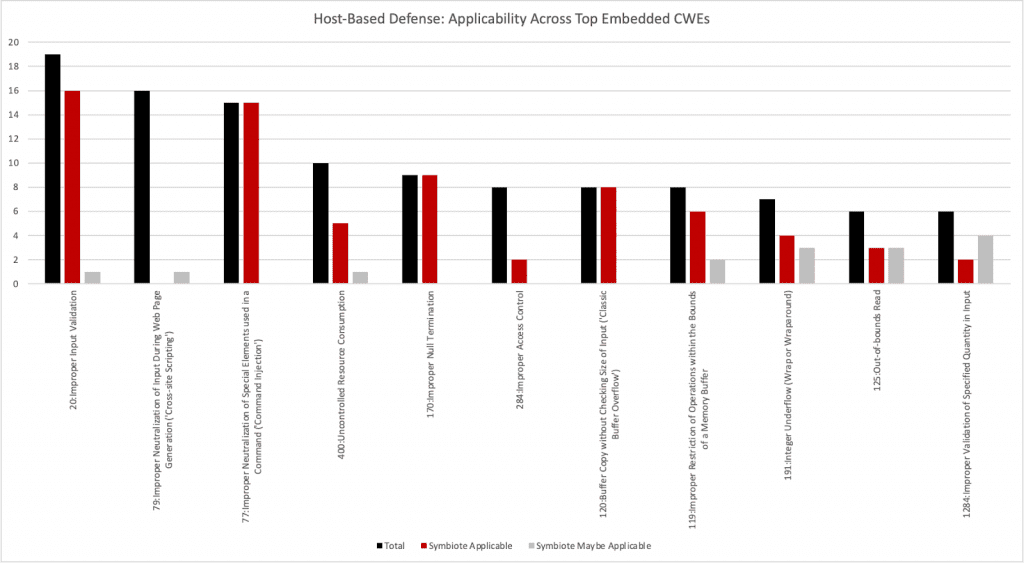
This is a breakdown that demonstrates host-based defense applicability to specific vulnerability types relevant to embedded systems.
The information included in device vulnerability advisories is not consistent. In some, there is an abundance of information and definite statements about the type of exploit an attacker could undertake. When, for example, a vulnerability is described as “buffer overflow that leads to remote code execution,” it is clear that host-based defense would be effective.
In contrast, with a vulnerability that allows “privilege escalation through a website and execution of OS-level commands,” host-based defense will be effective in some, but not all cases. If the commands being executed are meant to run on the device, host-based detection and response will not be remediative. It will be, however, if the commands should not be allowed when the device is deployed, but were incidentally included in the OS or firmware.
This accounts for the subset of results identified by the “host defense maybe” portion of the graphs above. Even in a highly selective analysis that does not consider these results, there is a strong case for the utility of host-based defenses for embedded devices and systems.
The percentage of disclosed vulnerabilities for which host-based defense will be applicable is almost certain to rise in the future, as vulnerabilities related to relatively simple engineering fixes (e.g. presence of hard-coded passwords) are resolved. More severe vulnerabilities associated with complex device controls and firmware can lead to remote code execution and other exploits, particularly given that attackers are increasingly targeting this level.
Data from Claroty’s H1 2022 ICS Risk & Vulnerability Report provides useful analysis that frames the value of host-based firmware defense. Here are some key findings:
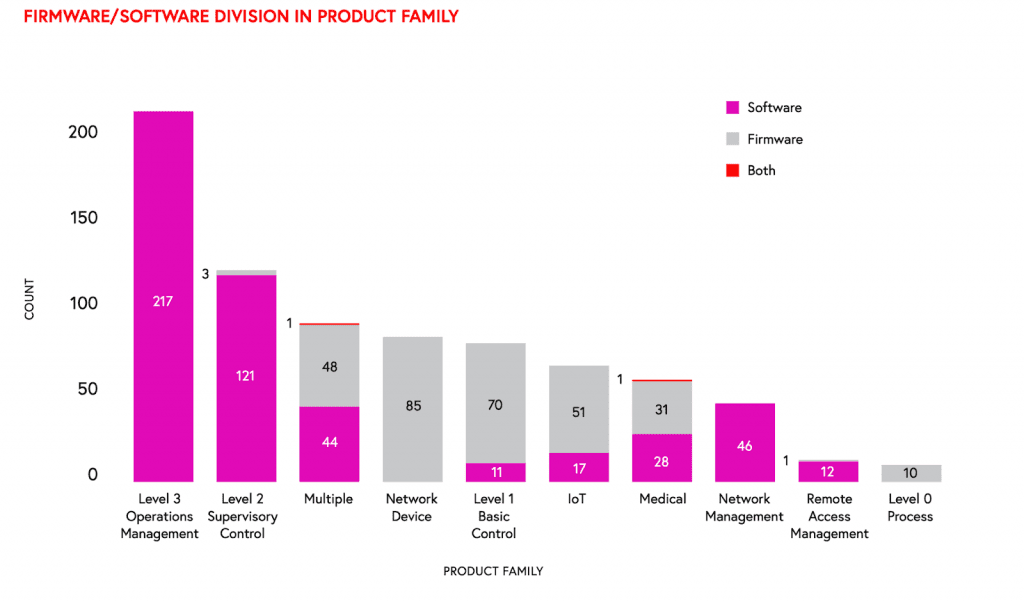
Source: Claroty ICS Risk & Vulnerability Report, H2 2021
Our analysis highlights two important realities: Vulnerabilities in OT systems are common, and at risk due to the reactive approach to patching.
Of course, not every vulnerability represents a serious or immediate attack opportunity. Attackers must work to formulate an exploit based on a published vulnerability, and also figure out how to reach the device in the field to run the exploit. Exploiting an unpublished or undiscovered vulnerability is even more challenging, as the attacker will need to undertake their own research and discovery process.
Also, we are not suggesting that the current cycle of discovery, disclosure and remediation is inherently flawed or in need of replacement. Given the quantity of published vulnerabilities and the uncountable number still undiscovered, DevOps and patching will be part of the security landscape for the foreseeable future.
But it is important to recognize that DevOps and patching can be a slow process, especially with firmware. It is not uncommon for the creation, testing and release of a firmware patch to require several months. Updates in safety certifications take even longer. Relying solely on these remediation mechanisms will not suffice; while still valuable, they must be augmented by technology that can respond in real time to zero-day attacks on undiscovered or unpatched vulnerabilities.
The findings in this analysis demonstrate the value of implementing security controls that detect anomalous behavior at the firmware level as a necessary extension of the reactive, “whack-a-mole” patching defense. These host-based defenses can provide a critical next step in device protection, and help to include embedded devices in a true “defense in depth” system.
We encourage you to review the accompanying data, and to learn more about how our firmware hardening, protection, and monitoring solutions can help your products and industrial systems achieve modern, proactive security.
We analyzed data from the national vulnerability database to assess the applicability of on-device security features
Whether they are discovered by independent researchers, manufacturers, or cyber attackers, device vulnerabilities traditionally have been remedied via patching. Although reactive, patching’s effectiveness is easy enough to quantify: It is effective if the vulnerability no longer exists after the patch is applied.
A host-based defense is another matter. It comprises technology that monitors a device’s function and issues alerts or remediations whenever malicious activity is detected. It does not remediate vulnerabilities: Rather, it defends against exploitation of an undiscovered or unremediated vulnerability.
As such, the host-based security apparatus’s effectiveness can be harder to evaluate than patching. There are several methods, including listing the controls enforced, mapping to a threat model, red teaming, or measuring the effectiveness of host-based defenses against current or likely, in the field, near-term attacks (“proven in use”).
And while “proven in use” evidence has obvious value, it is difficult to gather on host-based defenses (such as RBS’s Symbiote technology). The publicly available data on actual attacks is small, and there is good reason to believe it is often obscured or not released publicly.
Vulnerability disclosures provide some insights, as we can at least determine what types of attacks might be mounted against each vulnerability class. But no matter how severe it is, a device vulnerability only indicates a plausible means for a cyber attacker to gain a foothold on a device. Furthermore, the ongoing reality of zero-day vulnerabilities, which are not detected until a cyber incident is underway, requires a different way of thinking about, and defending against, attacks.
One way is to extrapolate from vulnerability data. This approach depends on several assumptions:
Host-based security is predicated on the need to move beyond a continuous cycle of patching. Vulnerabilities will always exist, and while the reactive patching process will continue to play a role in device security, it simply is not capable of deflecting a subset of threats that are not discovered or can’t be patched.
To evaluate host-based defense, we’ve used raw data published by the U.S. Cybersecurity & Infrastructure Security Agency-CISA on its ICS-Cert Advisories page. The entries include a rating based on the Common Vulnerability Scoring System (CVSS); risk evaluation; affected products, a Common Weakness Enumeration (CWE); and a vulnerability overview/analysis. The analysis is the key component that allows us to determine whether or not an attack launched against this vulnerability would be detected if a host-based defense technology was in place on the device.
Host-based security can benefit end users and original equipment manufacturers in terms of total cost of ownership and reputation:
Assessments of a host-based defense’s ability to detect and/or prevent attacks exploiting any particular vulnerability rely on the ICS Advisory’s risk evaluation, which highlights the class of weakness (CWE) to which the vulnerability belongs, and the consequences of the vulnerability’s exploit (e.g., remote code execution, buffer overflow, denial of service).
We reviewed approximately six months of ICS-Cert vulnerability disclosures. Of these, 37% were found in firmware.

Of the vulnerabilities with CVSS categorizations of “high” or “critical, almost 57% (157 of 276) are firmware-based:[1]

In our analysis, a host-based defense would be effective protection against 63% of these vulnerabilities, including all CVSS severity levels:

However, of the “high” or “critical” CVSS firmware vulnerabilities, a host-based defense could remove an attacker’s opportunity to reliably execute code or modify memory as part of an attack. It would be applicable or likely applicable on 74% of these vulnerabilities, and would reduce the CVSS rating for roughly one out of three, with an average decrease of 2.3 points on the CVSS scale.
More importantly, applying a host-based defense can reduce the severity of compromises to device integrity, confidentiality and availability. With CVSS vectors, a successful exploit would give an attacker the ability to gain full visibility into the devices’ functionality, and the ability to manipulate files and to deny access by legitimate users.

Our analysis found strong or universal host-based defense applicability with improper input validation, improper command injection, and classic buffer overflow:

This is a breakdown that demonstrates host-based defense applicability to specific vulnerability types relevant to embedded systems.
The information included in device vulnerability advisories is not consistent. In some, there is an abundance of information and definite statements about the type of exploit an attacker could undertake. When, for example, a vulnerability is described as “buffer overflow that leads to remote code execution,” it is clear that host-based defense would be effective.
In contrast, with a vulnerability that allows “privilege escalation through a website and execution of OS-level commands,” host-based defense will be effective in some, but not all cases. If the commands being executed are meant to run on the device, host-based detection and response will not be remediative. It will be, however, if the commands should not be allowed when the device is deployed, but were incidentally included in the OS or firmware.
This accounts for the subset of results identified by the “host defense maybe” portion of the graphs above. Even in a highly selective analysis that does not consider these results, there is a strong case for the utility of host-based defenses for embedded devices and systems.
The percentage of disclosed vulnerabilities for which host-based defense will be applicable is almost certain to rise in the future as vulnerabilities related to relatively simple engineering fixes (e.g. presence of hard-coded passwords) are resolved. More severe vulnerabilities associated with complex device controls and firmware can lead to remote code execution and other exploits, particularly given that attackers are increasingly targeting this level.
Data from Claroty’s H1 2022 ICS Risk & Vulnerability Report provides useful analysis that frames the value of host-based firmware defense. Here are some key findings:

Source: Claroty ICS Risk & Vulnerability Report, H2 2021
Our analysis highlights two important realities: Vulnerabilities in OT systems are common, and at risk due to the reactive approach to patching.
Of course, not every vulnerability represents a serious or immediate attack opportunity. Attackers must work to formulate an exploit based on a published vulnerability, and also figure out how to reach the device in the field to run the exploit. Exploiting an unpublished or undiscovered vulnerability is even more challenging, as the attacker will need to undertake their own research and discovery process.
Also, we are not suggesting that the current cycle of discovery, disclosure and remediation is inherently flawed or in need of replacement. Given the quantity of published vulnerabilities and the uncountable number still undiscovered, DevOps and patching will be part of the security landscape for the foreseeable future.
But it is important to recognize that DevOps and patching can be a slow process, especially with firmware. It is not uncommon for the creation, testing and release of a firmware patch to require several months. Updates in safety certifications take even longer. Relying solely on these remediation mechanisms will not suffice; while still valuable, they must be augmented by technology that can respond in real time to zero day attacks on undiscovered or unpatched vulnerabilities.
The findings in this analysis demonstrate the value of implementing security controls that detect anomalous behavior at the firmware level as a necessary extension of the reactive, “whack-a-mole” patching defense. These host-based defenses can provide a critical next step in device protection, and help to include embedded devices in a true “defense in depth” system.
We encourage you to review the accompanying data, and to learn more about how our firmware hardening, protection, and monitoring solutions can help your products and industrial systems achieve modern, proactive security.
We analyzed data from the national vulnerability database to assess the applicability of on-device security features
Whether they are discovered by independent researchers, manufacturers, or cyber attackers, device vulnerabilities traditionally have been remedied via patching. Although reactive, patching’s effectiveness is easy enough to quantify: It is effective if the vulnerability no longer exists after the patch is applied.
A host-based defense is another matter. It comprises technology that monitors a device’s function and issues alerts or remediations whenever malicious activity is detected. It does not remediate vulnerabilities: Rather, it defends against exploitation of an undiscovered or unremediated vulnerability.
As such, the host-based security apparatus’s effectiveness can be harder to evaluate than patching. There are several methods, including listing the controls enforced, mapping to a threat model, red teaming, or measuring the effectiveness of host-based defenses against current or likely, in the field, near-term attacks (“proven in use”).
And while “proven in use” evidence has obvious value, it is difficult to gather on host-based defenses (such as RBS’s Symbiote technology). The publicly available data on actual attacks is small, and there is good reason to believe it is often obscured or not released publicly.
Vulnerability disclosures provide some insights, as we can at least determine what types of attacks might be mounted against each vulnerability class. But no matter how severe it is, a device vulnerability only indicates a plausible means for a cyber attacker to gain a foothold on a device. Furthermore, the ongoing reality of zero-day vulnerabilities, which are not detected until a cyber incident is underway, requires a different way of thinking about, and defending against, attacks.
One way is to extrapolate from vulnerability data. This approach depends on several assumptions:
Host-based security is predicated on the need to move beyond a continuous cycle of patching. Vulnerabilities will always exist, and while the reactive patching process will continue to play a role in device security, it simply is not capable of deflecting a subset of threats that are not discovered or can’t be patched.
To evaluate host-based defense, we’ve used raw data published by the U.S. Cybersecurity & Infrastructure Security Agency-CISA on its ICS-Cert Advisories page. The entries include a rating based on the Common Vulnerability Scoring System (CVSS); risk evaluation; affected products, a Common Weakness Enumeration (CWE); and a vulnerability overview/analysis. The analysis is the key component that allows us to determine whether or not an attack launched against this vulnerability would be detected if a host-based defense technology was in place on the device.
Host-based security can benefit end users and original equipment manufacturers in terms of total cost of ownership and reputation:
Assessments of a host-based defense’s ability to detect and/or prevent attacks exploiting any particular vulnerability rely on the ICS Advisory’s risk evaluation, which highlights the class of weakness (CWE) to which the vulnerability belongs, and the consequences of the vulnerability’s exploit (e.g., remote code execution, buffer overflow, denial of service).
We reviewed approximately six months of ICS-Cert vulnerability disclosures. Of these, 37% were found in firmware.

Of the vulnerabilities with CVSS categorizations of “high” or “critical, almost 57% (157 of 276) are firmware-based:[1]

In our analysis, a host-based defense would be effective protection against 63% of these vulnerabilities, including all CVSS severity levels:

However, of the “high” or “critical” CVSS firmware vulnerabilities, a host-based defense could remove an attacker’s opportunity to reliably execute code or modify memory as part of an attack. It would be applicable or likely applicable on 74% of these vulnerabilities, and would reduce the CVSS rating for roughly one out of three, with an average decrease of 2.3 points on the CVSS scale.
More importantly, applying a host-based defense can reduce the severity of compromises to device integrity, confidentiality and availability. With CVSS vectors, a successful exploit would give an attacker the ability to gain full visibility into the devices’ functionality, and the ability to manipulate files and to deny access by legitimate users.

Our analysis found strong or universal host-based defense applicability with improper input validation, improper command injection, and classic buffer overflow:

This is a breakdown that demonstrates host-based defense applicability to specific vulnerability types relevant to embedded systems.
The information included in device vulnerability advisories is not consistent. In some, there is an abundance of information and definite statements about the type of exploit an attacker could undertake. When, for example, a vulnerability is described as “buffer overflow that leads to remote code execution,” it is clear that host-based defense would be effective.
In contrast, with a vulnerability that allows “privilege escalation through a website and execution of OS-level commands,” host-based defense will be effective in some, but not all cases. If the commands being executed are meant to run on the device, host-based detection and response will not be remediative. It will be, however, if the commands should not be allowed when the device is deployed, but were incidentally included in the OS or firmware.
This accounts for the subset of results identified by the “host defense maybe” portion of the graphs above. Even in a highly selective analysis that does not consider these results, there is a strong case for the utility of host-based defenses for embedded devices and systems.
The percentage of disclosed vulnerabilities for which host-based defense will be applicable is almost certain to rise in the future as vulnerabilities related to relatively simple engineering fixes (e.g. presence of hard-coded passwords) are resolved. More severe vulnerabilities associated with complex device controls and firmware can lead to remote code execution and other exploits, particularly given that attackers are increasingly targeting this level.
Data from Claroty’s H1 2022 ICS Risk & Vulnerability Report provides useful analysis that frames the value of host-based firmware defense. Here are some key findings:

Source: Claroty ICS Risk & Vulnerability Report, H2 2021
Our analysis highlights two important realities: Vulnerabilities in OT systems are common, and at risk due to the reactive approach to patching.
Of course, not every vulnerability represents a serious or immediate attack opportunity. Attackers must work to formulate an exploit based on a published vulnerability, and also figure out how to reach the device in the field to run the exploit. Exploiting an unpublished or undiscovered vulnerability is even more challenging, as the attacker will need to undertake their own research and discovery process.
Also, we are not suggesting that the current cycle of discovery, disclosure and remediation is inherently flawed or in need of replacement. Given the quantity of published vulnerabilities and the uncountable number still undiscovered, DevOps and patching will be part of the security landscape for the foreseeable future.
But it is important to recognize that DevOps and patching can be a slow process, especially with firmware. It is not uncommon for the creation, testing and release of a firmware patch to require several months. Updates in safety certifications take even longer. Relying solely on these remediation mechanisms will not suffice; while still valuable, they must be augmented by technology that can respond in real time to zero day attacks on undiscovered or unpatched vulnerabilities.
The findings in this analysis demonstrate the value of implementing security controls that detect anomalous behavior at the firmware level as a necessary extension of the reactive, “whack-a-mole” patching defense. These host-based defenses can provide a critical next step in device protection, and help to include embedded devices in a true “defense in depth” system.
We encourage you to review the accompanying data, and to learn more about how our firmware hardening, protection, and monitoring solutions can help your products and industrial systems achieve modern, proactive security.
[1] CVSS scores depend on a rubric that considers multiple variables, including the distance an attacker can be from a target; whether or not the attacker can perform the attack at will; whether or not any user interaction is required; the number of privileges that are required; whether or not systems beyond the vulnerable component can be impacted; the amount of information that may be disclosed; the amount of information that can be modified; and the degree of disruption to availability. For a detailed description of the scoring, see https://www.first.org/cvss/user-guide.
[1] CVSS scores depend on a rubric that considers multiple variables, including the distance an attacker can be from a target; whether or not the attacker can perform the attack at will; whether or not any user interaction is required; the number of privileges that are required; whether or not systems beyond the vulnerable component can be impacted; the amount of information that may be disclosed; the amount of information that can be modified; and the degree of disruption to availability. For a detailed description of the scoring, see https://www.first.org/cvss/user-guide.
[1] CVSS scores depend on a rubric that considers multiple variables, including the distance an attacker can be from a target; whether or not the attacker can perform the attack at will; whether or not any user interaction is required; the number of privileges that are required; whether or not systems beyond the vulnerable component can be impacted; the amount of information that may be disclosed; the amount of information that can be modified; and the degree of disruption to availability. For a detailed description of the scoring, see https://www.first.org/cvss/user-guide.

Contact us now to discover more about Red Balloon Security’s range of solutions and services or to arrange a demonstration.

Reach out to learn more about our embedded security offering and to schedule a demo.

Reach out to learn more about our embedded security offering and to schedule a demo.
Reach out to learn more about our embedded security offering and to schedule a demo.