RBS’s core technology is highly effective in any embedded device environment, from cars to heavy industry, because it does not require access to source code, or any hardware modifications.
On-device security is still controversial. Some industry professionals and manufacturers push back against the very idea of it because of an outdated conviction that devices deep in the technology stack are beyond the reach of cyberattack, or simply do not present a sufficiently attractive target. Others believe that embedded devices do not have the resources to support a robust on-host security.
Red Balloon’s research is a strong proof point against the idea that this level of security isn’t needed. And on-device security is becoming more common, as firewalls and encrypted protocols have been introduced to many endpoints at this level.
But runtime monitoring and protection, such as Red Balloon’s Symbiote technology, has yet to be widely accepted, and many of our potential customers cite limited device resources as an impediment. While convinced of the utility and necessity of embedded security, some remain concerned that any manipulation of device firmware will result in decreased effectiveness, regular crashes, or even terminal inoperability.
Given the sophisticated engineering of these devices, the caution is understandable. But Symbiote technology prioritizes device functionality. In addition to defending against n-day and zero-day attacks, including those that bypass traditional security controls, the Symbiote integration process uses advanced firmware analysis, unpacking, and repacking technology to prevent any damage or compromise of the original device firmware.
The combination of technologies executes the dual functions of improving device security and protecting core device functionality.
Symbiote is not an out-of-the-box solution. As with other embedded device technologies, deployment on a device requires time, and it must be carried out by skilled professionals to ensure safe, correct device operation. Red Balloon engineers typically undertake a thorough analysis of the device and its functionality before a Symbiote deployment is attempted.
We have seen a gradual adoption of device security before. The introduction of endpoint protections such as firewalls, antivirus and access controls to devices in control rooms, without disrupting operation, also required skilled and dedicated engineering. Early adopters received a two-fold benefit from this careful approach: They received security before their competitors, and built in time to deal with unavoidable complications, without serious disruption to their processes.
Today, operators who rely on embedded devices are at a similar juncture. They can begin a security upgrade within a window that allows sufficient time to improve devices and the security tools deployed on them. The window may be closing, as embedded devices are increastingly targeted by malicious actors in many systems. But we are confident that ultimately, security deployments on these devices will be as simple and non-disruptive as they are for other endpoints in the technology stack.[1]
Symbiote injection depends on interrelated technologies that identify and remove extraneous code from the host firmware; randomize the firmware; unpack, analyze, and repack the firmware; and deploy Symbiote payloads into the firmware. These include:
Open Firmware Reverse Analysis Konsole (OFRAK): OFRAK is a framework for unpacking, analyzing, modifying, and repacking a device’s firmware images. It is the technological framework through which automated firmware hardening is performed and Symbiotes are integrated. The OFRAK framework is a force-multiplier tool — and it integrates into any development environment.
OFRAK does not require source code, and operates on binaries. However, device manufacturers typically supply a development binary that includes debugging symbols, and a means to load modified firmware binaries on the device to aid analysis. (It is possible to analyze and identify firmware components without the above, and this may be required when Red Balloon engages a device end user who does not have access to the files.)
The OFRAK unpacking engine will analyze all the firmware call tables and functions to determine how and when firmware objects come into operation, which can be removed, and what parts support core functions. This analysis sets up the initial stages of firmware modification: binary reduction and binary structure randomization.
Binary reduction, via ABR, serves the dual purpose of hardening the firmware by removing extraneous code (which could be exploited by an attacker) and creating space for the injection of Symbiotes. ABR automatically maps call paths, and builds out a code graph that identifies services and information that is never called, or should not be called.
This extraneous code can either be safely removed or replaced with a stub that allows the firmware to continue running without risk of a code crash. The binary reduction creates space in the firmware image, and can help the device to work faster. ABR also generates a report of all changes to facilitate review.
With the binary reduction complete, the firmware code can be randomized by advanced polymorphic engines that create a distinct new code, which can defeat attacks that rely on knowledge of code layout. The BSR function then utilizes the space created by ABR and moves blocks of code and memory, identifies all places where the original function was removed, and updates the call map.
Combined, ABR and BSR provide important additional layers of security while maintaining a meticulous record of the original firmware, every change in code and a map of the new firmware image.[2]
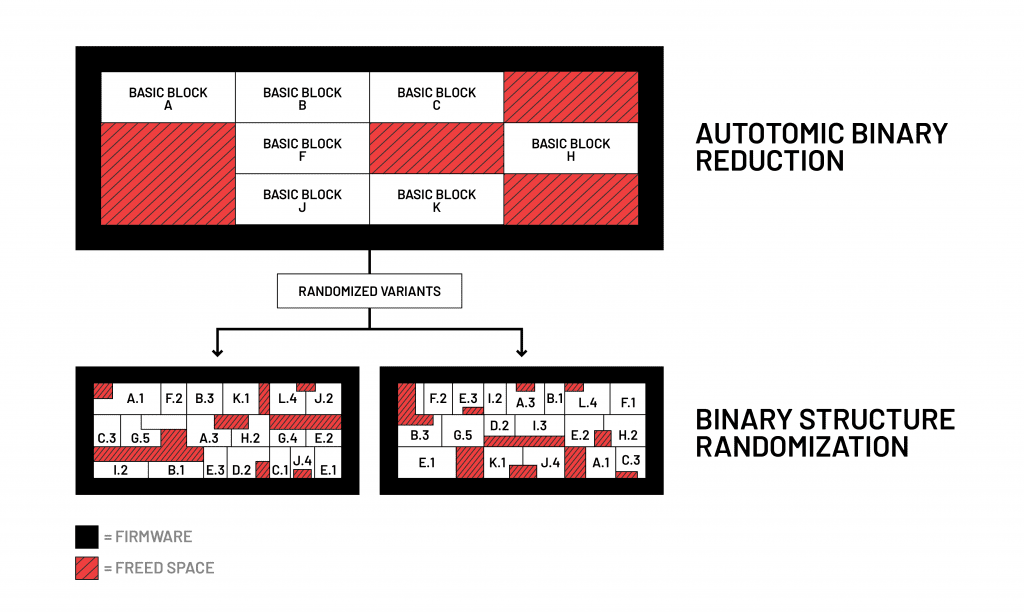
ABR and BSR work in sequence, with ABR first removing unused pieces of binary code and BSR using the freed space to create a randomized — and therefore stronger — firmware structure.
Source code is often proprietary, and many companies are understandably reluctant to allow third parties to access it or refine it. By working in binary, copyright issues can be avoided, leaving the manufacturer to update the source code once the binary modification is complete. The new firmware is functionally equivalent to the original, which facilitates future source code updates. In some cases, an end user may wish to update a device for which the original source code is not available.
The process for injecting the Symbiotes includes automatic identification of a large number of injection points, and the selection of a random subset for Symbiote invocation. This means each randomized instance is distinct from all other injected systems.
The process begins by identifying every function in the firmware through analysis of the binary. This leads to the identification of usable, or “hookable” functions into which the Symbiotes can be injected without any disruption of normal operation .
The Symbiote injection process is designed to balance detection resolution functionality with the device workload requirements. It dynamically utilizes CPU cycles from the host device at intervals via an adaptive scheduler that helps prevent an injected Symbiote from adversely impacting performance or corrupting the device firmware. As independent digital “life forms,” the Symbiotes co-exist with arbitrary executables in a mutually defensive arrangement. As such, Symbiotes are designed to simultaneously protect their host through their detection capabilities while maintaining the parameters for core functionality.
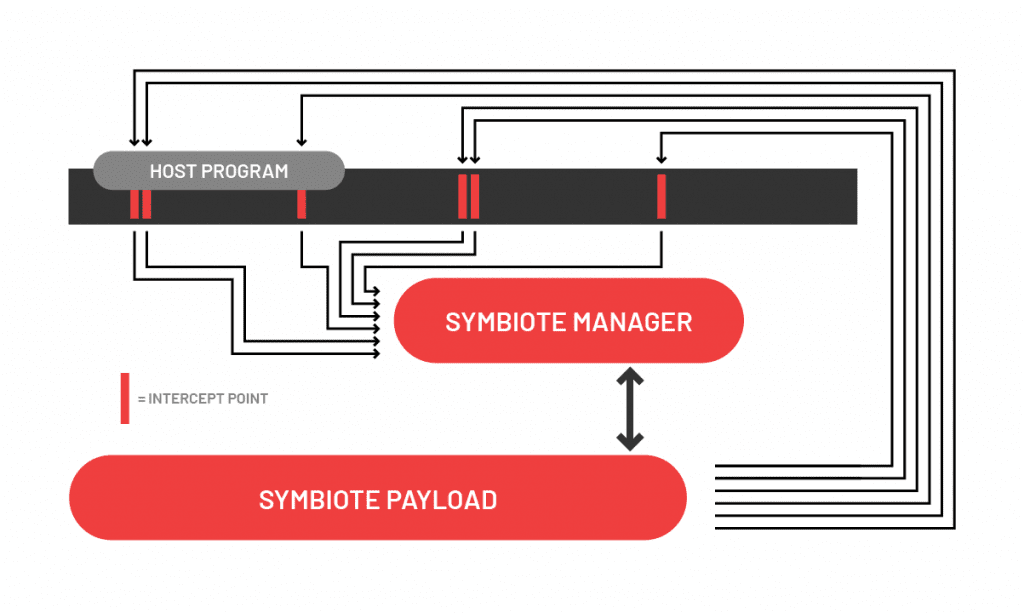
Each intercept point, or “hook,” is a potential injection point. The Symbiote manager maintains visibility of the device function to detect any interference with core functionality or at instances with low CPU utilization.
A Symbiote is a code structure embedded in situ into the firmware of an embedded system. The Symbiote tightly co-exists with its host executable in a mutually defensive arrangement, sharing computational resources with its host while simultaneously protecting the host against exploitation and unauthorized modification.
Each Symbiote includes a payload (the actual defensive mechanism), a manager (which ensures the native OS can safely execute, and prevents the native OS from overwriting the memory chunks used to store payloads’ execution context records) and user-defined policy engine (which has a checksum of every new process that runs and automatically compares this against the device user’s defined whitelist of known, allowed processes).
Once the injection points are established, OFRAK repackages the firmware to its original state, with the addition of the Symbiote payloads. The repacking engine uses the call tables and unpacking analysis to establish that all functions remain intact.
At this point in the process, it is possible that Symbiote scheduler configurations will need to be tuned to avoid peaking the processing load or interrupting essential functionality. This process typically is undertaken in coordination with the device manufacturer, who can provide performance overhead and detection latency goals to help establish the modified firmware will run as expected in its field deployment.
The goal is to establish a percentage of baseload Symbiote can utilize and which processes can never be interrupted. The tuning process allows the engineers to make adjustments if these parameters are not adhered to after injection. The vendor’s input at this stage can be useful, since their engineering staff should have a native understanding of the device functionality. That said, Red Balloon’s research staff has abundant resources and device firmware expertise to leverage when assistance is necessary.
Red Balloon encourages device manufacturers to use a firmware signature verification process once the Symbiote injection and tuning is complete.
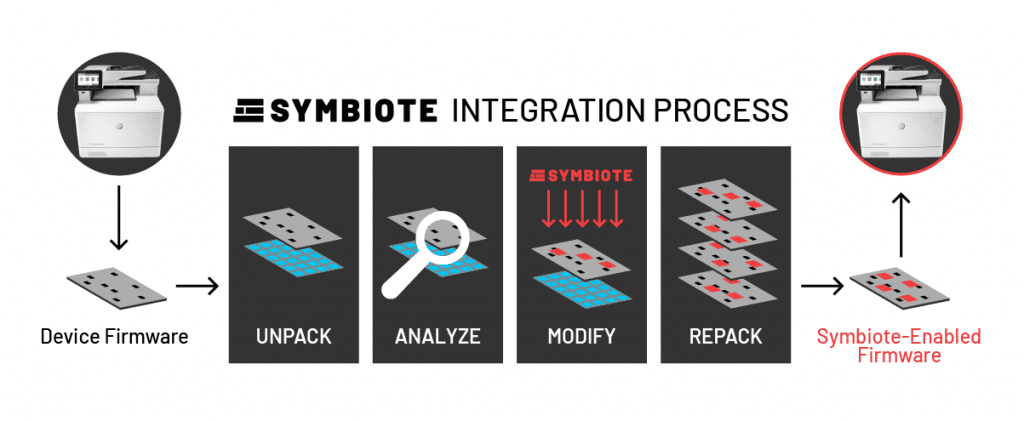
The Symbiote injection process creates modified firmware that must be tuned to avoid function interference and minimize process
Antivirus is blacklist technology that must be installed onto or into an operating system, which makes it dependent on that system’s features and integrity, and subject to regular updates.
By contrast, Symbiotes do not operate on top of or as part of the protected application or operating system. They are infused into a protected executable that does not depend on a trust relationship with its host. Since it looks for effects and changes, it operates as a whitelist, and does not require regular updates. Symbiote also can protect all the levels of the device, including bootloader, OS, applications and memory.
Symbiote injection is a mature process that has enabled billions of hours of error-free runtime on devices in the field and many more in testing deployments. The deployment process involves tuning, and the firmware adaptation may initially pull an excessive number of CPU cycles or interfere with functions that are necessary to device functionality. This is why the multi-step implementation and testing process is essential.
Red Balloon has leveraged its extensive knowledge of device or reverse engineering to develop a security technology that is OS-agnostic and can be deployed without any available source code. That said, we recognize and value the device manufacturer’s knowledge of their product. At this stage of Symbiote’s evolution, an OEM’s detailed knowledge can still be tremendously beneficial to our engineering process. Our willingness to work with other engineers through a mutually supportive technology build process is critical to establishing a new standard for embedded device technology.
[1] Symbiote behavior during runtime and reporting also maintains device integrity, and will be covered in a separate article. Here we are focused on the process of building hardened firmware, into which symbiotes can be inserted, and the actual injection of the symbiotes.
[2] In some instances, the OFRAK process may identify sufficient Symbiote injection points without requiring any binary reduction and/or randomization.