Programmable logic controllers (PLCs) are critical embedded devices used in modern industrial environments. The Siemens S7-1500 is an industry-leading, high-performance controller that is considered to possess comprehensive security protections amongst Siemens PLC products.
Over the past 10 years, Red Balloon Security has conducted extensive research on the security of embedded systems including PLCs, protection relays, building automation controllers, networking equipment, telecommunications infrastructure, and satellite ground control system infrastructure. Red Balloon’s previous research that specifically focused on Root of Trust (RoT) implementations resulted in discovery of a vulnerability disclosed in 2019 called “Thrangrycat”, which allows for persistent bypass of Cisco’s proprietary secure boot mechanism. Thrangrycat is caused by a series of hardware design flaws within Cisco’s Trust Anchor module (TAm) that allows an attacker to make persistent modification to the TAm via FPGA bitstream modification, thereby defeating the secure boot process and invalidating Cisco’s chain of trust at its root.
Red Balloon’s latest research consists of discovering multiple, critical architectural vulnerabilities in the Siemens S7-1500 series that allow for bypass of all protected boot features. This discovery has potentially significant implications for industrial environments as these unpatchable hardware root-of-trust vulnerabilities could result in persistent arbitrary modification of S7-1500 operating code and data. Exploitation of these vulnerabilities could allow offline attackers to generate arbitrary encrypted firmware that are bootable on all Siemens S7-1500 series PLC CPU modules. Furthermore, these vulnerabilities allow attackers to persistently bypass integrity validation and security features of the ADONIS operating system and subsequent user space code. Red Balloon has reported these vulnerabilities to Siemens, and Siemens has confirmed them.
The vulnerabilities exist because the Siemens custom System-on-Chip (SoC) does not establish a tamper proof Root of Trust (RoT) in the early boot process. The Siemens RoT is implemented through the integration of a dedicated cryptographic secure element — the ATECC CryptoAuthentication chip. However, this architecture contains flaws that can be leveraged to compromise the system. Failure to establish a RoT on the device allows attackers to load custom-modified bootloaders and firmware.
The fundamental vulnerabilities — improper hardware implementations of the RoT using dedicated cryptographic-processor — are unpatchable and cannot be fixed by a firmware update since the hardware is physically unmodifiable. To limit the effects of potential exploitation of these vulnerabilities, Red Balloon has recommended several mitigations to Siemens which include: implement runtime integrity attestation; add asymmetric signature check for firmware at bootup scheme; and encrypt the firmware with device specific keys that are generated on individual devices.
Red Balloon has developed an advanced persistent threat detection tool for owners and operators of the Siemens S7-1500 series PLCs to verify whether vulnerable devices have been tampered with or compromised.
Siemens released the following list of more than 100 products with this vulnerability with currently no fix available.
The ATECC CryptoAuthentication-based RoT hardware implementation is vulnerable and deployed across the Siemens S7-1500 series product line. The firmware gets decrypted in memory and executed each time during bootup. The decryption keys are not built into the firmware itself. Instead, a physical secure element chip — the ATECC108 CryptoAuthentication coprocessor — is used to calculate a decryption seed based on the firmware metadata (header) and the master key inside the secure element. The decryption seed then derives the AES keys for different parts of the encrypted firmware.
However, this ATECC CryptoAuthentication implementation contains flaws that can be leveraged to compromise the integrity of the system. The secure element shared secret is exposed, as shown in Figure 1, which allows attackers to abuse the secure element. The shared secret resides in the device’s nonvolatile storage which can be accessed by attackers. The CryptoAuthentication chip can be used as an oracle to generate the decryption seed which is used to derive AES keys for encrypted firmware. The plaintext bootloader reveals the firmware AES key derivation and decryption scheme.
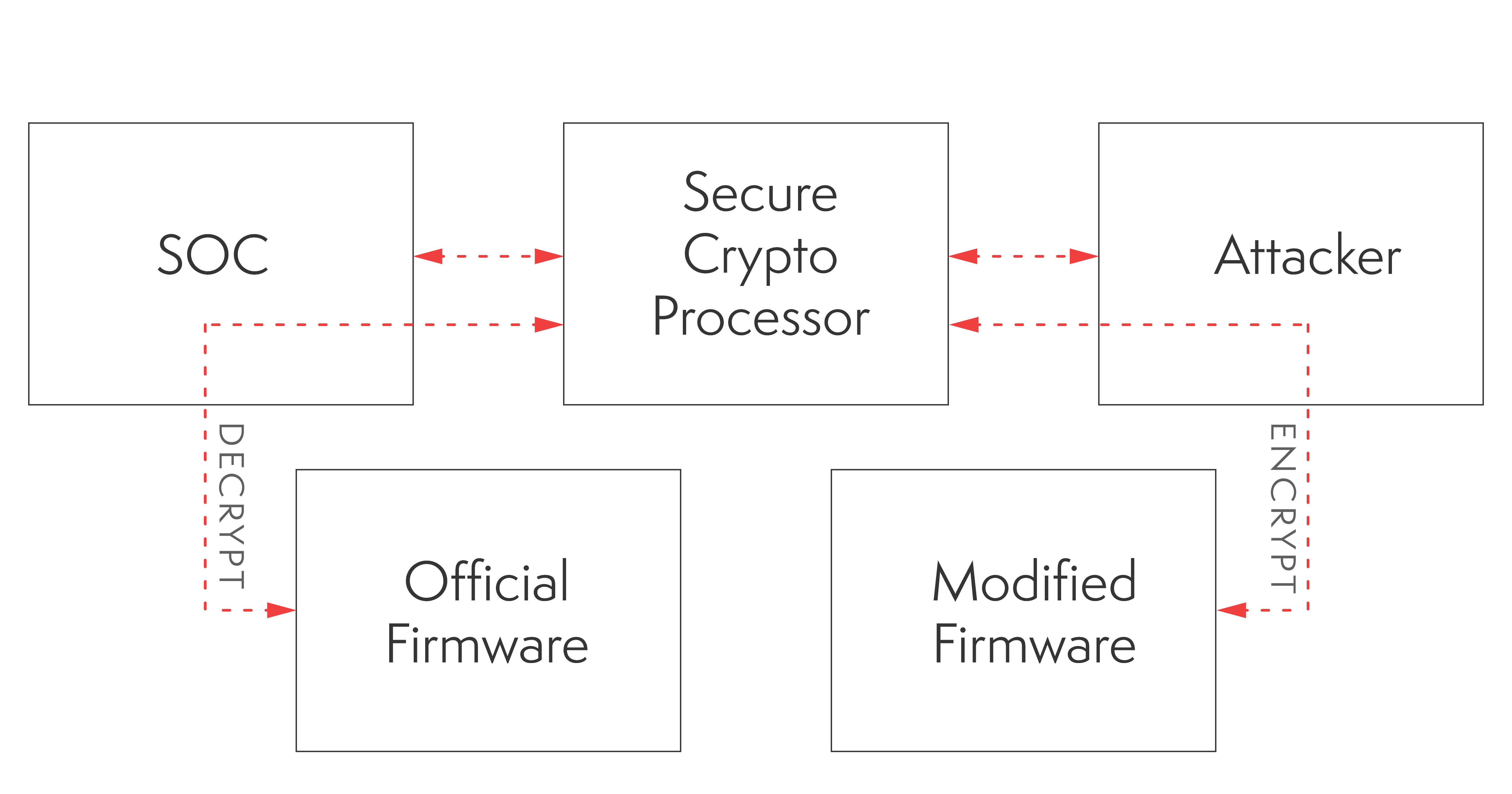
This attack flow allows an attacker to load a custom-modified bootloader and firmware to vulnerable Siemens S7-1500 series PLCs.
The Siemens S7-1500 series PLCs implement a boot-time firmware validation scheme using a combination of hardware-enabled firmware decryption and binary integrity validation in the Siemens ADONIS operating system. Multiple architectural vulnerabilities exist which allow attackers to bypass all protected boot features, resulting in persistent arbitrary modification of operating code and data. With physical access to a single device, attackers can exploit the vulnerabilities to generate valid AES keys for most of the S7-1500 series firmwares, including the one modified by attackers. The custom-modified firmware can be authenticated and decrypted by the original boot process. By flashing this malicious firmware on a target device, either physically or by exploiting an existing remote code execution vulnerability, attackers could persistently gain arbitrary code execution and potentially circumvent any official security and firmware updates, without the user’s knowledge.
Red Balloon would like to thank Siemens for its response in confirming our findings and coordination in the disclosure process.
Programmable logic controllers (PLCs) are critical embedded devices used in modern industrial environments. The Siemens S7-1500 is an industry-leading, high-performance controller that is considered to possess comprehensive security protections amongst Siemens PLC products.
Over the past 10 years, Red Balloon Security has conducted extensive research on the security of embedded systems including PLCs, protection relays, building automation controllers, networking equipment, telecommunications infrastructure, and satellite ground control system infrastructure. Red Balloon’s previous research that specifically focused on Root of Trust (RoT) implementations resulted in discovery of a vulnerability disclosed in 2019 called “Thrangrycat”, which allows for persistent bypass of Cisco’s proprietary secure boot mechanism. Thrangrycat is caused by a series of hardware design flaws within Cisco’s Trust Anchor module (TAm) that allows an attacker to make persistent modification to the TAm via FPGA bitstream modification, thereby defeating the secure boot process and invalidating Cisco’s chain of trust at its root.
Red Balloon’s latest research consists of discovering multiple, critical architectural vulnerabilities in the Siemens S7-1500 series that allow for bypass of all protected boot features. This discovery has potentially significant implications for industrial environments as these unpatchable hardware root-of-trust vulnerabilities could result in persistent arbitrary modification of S7-1500 operating code and data. Exploitation of these vulnerabilities could allow offline attackers to generate arbitrary encrypted firmware that are bootable on all Siemens S7-1500 series PLC CPU modules. Furthermore, these vulnerabilities allow attackers to persistently bypass integrity validation and security features of the ADONIS operating system and subsequent user space code. Red Balloon has reported these vulnerabilities to Siemens, and Siemens has confirmed them.
The vulnerabilities exist because the Siemens custom System-on-Chip (SoC) does not establish a tamper proof Root of Trust (RoT) in the early boot process. The Siemens RoT is implemented through the integration of a dedicated cryptographic secure element — the ATECC CryptoAuthentication chip. However, this architecture contains flaws that can be leveraged to compromise the system. Failure to establish a RoT on the device allows attackers to load custom-modified bootloaders and firmware.
The fundamental vulnerabilities — improper hardware implementations of the RoT using dedicated cryptographic-processor — are unpatchable and cannot be fixed by a firmware update since the hardware is physically unmodifiable. To limit the effects of potential exploitation of these vulnerabilities, Red Balloon has recommended several mitigations to Siemens which include: implement runtime integrity attestation; add asymmetric signature check for firmware at bootup scheme; and encrypt the firmware with device specific keys that are generated on individual devices.
Red Balloon has developed an advanced persistent threat detection tool for owners and operators of the Siemens S7-1500 series PLCs to verify whether vulnerable devices have been tampered with or compromised.
Siemens released the following list of more than 100 products with this vulnerability with currently no fix available.
The ATECC CryptoAuthentication-based RoT hardware implementation is vulnerable and deployed across the Siemens S7-1500 series product line. The firmware gets decrypted in memory and executed each time during bootup. The decryption keys are not built into the firmware itself. Instead, a physical secure element chip — the ATECC108 CryptoAuthentication coprocessor — is used to calculate a decryption seed based on the firmware metadata (header) and the master key inside the secure element. The decryption seed then derives the AES keys for different parts of the encrypted firmware.
However, this ATECC CryptoAuthentication implementation contains flaws that can be leveraged to compromise the integrity of the system. The secure element shared secret is exposed, as shown in Figure 1, which allows attackers to abuse the secure element. The shared secret resides in the device’s nonvolatile storage which can be accessed by attackers. The CryptoAuthentication chip can be used as an oracle to generate the decryption seed which is used to derive AES keys for encrypted firmware. The plaintext bootloader reveals the firmware AES key derivation and decryption scheme.

This attack flow allows an attacker to load a custom-modified bootloader and firmware to vulnerable Siemens S7-1500 series PLCs.
The Siemens S7-1500 series PLCs implement a boot-time firmware validation scheme using a combination of hardware-enabled firmware decryption and binary integrity validation in the Siemens ADONIS operating system. Multiple architectural vulnerabilities exist which allow attackers to bypass all protected boot features, resulting in persistent arbitrary modification of operating code and data. With physical access to a single device, attackers can exploit the vulnerabilities to generate valid AES keys for most of the S7-1500 series firmwares, including the one modified by attackers. The custom-modified firmware can be authenticated and decrypted by the original boot process. By flashing this malicious firmware on a target device, either physically or by exploiting an existing remote code execution vulnerability, attackers could persistently gain arbitrary code execution and potentially circumvent any official security and firmware updates, without the user’s knowledge.
Red Balloon would like to thank Siemens for its response in confirming our findings and coordination in the disclosure process.
© 2025 Red Balloon Security.
All Rights Reserved.
Sal Stolfo was an original founding member of Red Balloon Security, Inc.
Contact us to learn more about our advanced embedded security solutions or schedule a demonstration with our experts.